Tuesday, January 5, 2010
iPhone tricks, tips and apps for attorneys - Webinar
iPhone Tips, Tricks and Apps for Lawyers
Friday, January 8th at 1:00 EST
Register At - http://execsense.com/details.asp?id=433 or Call (415) 453-3003
In iPhone Tips, Tricks & Apps for Lawyers, ExecSense shares quick and easy ways to
truly capitalize on all that an iPhone has to offer for a lawyer. Take the 60 minutes to
view this webinar (on your computer, mobile phone, iPod or printed out) to update your
knowledge on how other lawyers are getting the most out of their iPhones, as many
features, settings and new applications are not used by lawyers that can significantly
improve it's value to you as a resource, as long as you know how to use them.
If you cannot call-in to attend the webinar and view the presentation at 1:00 EST Friday,
January 8th, ExecSense will email you the PowerPoint, audio and supplementary files by
the next day for viewing at your convenience (you simply need to register before the
webinar occurs). The webinar is led by Ahmer Khan, an expert on helping lawyers get
the most out of their iPhones, and focuses on:
A tour of your iPhone, specifically for lawyers, with suggestions, tips and tricks on
doing more with your email, phone, contacts, messages/sms and calendar
A list of 15 must-have applications for lawyers, how to easily install and use them,
and why it will immediately make you more productive and efficient while away
from the office.
Price: $250 (1 Person) or $500 (Access All Webinars for 1 Year & Free Pass for
Colleague to Attend This Webinar)
------------------------------------------------
Wednesday, December 23, 2009
ACBA Articles on Netbooks / Law Firm Websites
- Netbooks Offer a Lightweight and Wireless Computer Option (page 5)
- Law Firm Website Basics: From Design to Content (page 6)
Read both articles here:
http://www.acba.org/ACBA/Publications/Lawyers-Journal.asp
--------------------------------------------------
Monday, November 30, 2009
ABA Journal Reviews Google Scholar
Users can go to the Google Scholar online search engine and type in case names, topics or key words to find the relevant cases. “We think this addition to Google Scholar will empower the average citizen by helping everyone learn more about the laws that govern us all,” Google says in an announcement posted at TaxProf Blog.
http://www.abajournal.com/news/article/google_offers_legal_research_for_the_average_citizenand_lawyers_too
---------------------------------------------------------------------
Thursday, November 19, 2009
Google Scholar: The Next Westlaw/Lexis Nexis?

Looking for that hard to find court decision or administrative ruling? Maybe it is outside your subscription? Google Scholar may be your answer. Even better...it is free.
http://scholar.google.com/
Simply type in the case and/or citation you are looking for and hit the "Search" button and a list of potential websites with that citation or case will soon appear. Although the service is not perfect, and may not have a lot of specialized holdings, it is a promising tool.
Read more about the service here.
Thanks to WBA Member Christopher Watson for sending this concept to the WBA Blog!
-------------------------------------------------
Wednesday, October 7, 2009
Technology Tip: Internet Cookies - Good or Bad?
When you access a website, the site usually (but not always) collects information about your visit, storing it in a small text file on your computer called a cookie. You may even be prompted with a remember me on this website. On each subsequent visit, the website retrieves this information from your hard drive, with the idea of personalizing your visit based on previously expressed preferences or browsing history. After each visit, the cookie is updated and stored again on your hard drive.
Cookies typically contain information such as language preference, previously entered options for number and arrangements of items to display, perhaps the contents of an unfinished shopping cart, and so on. Cookies from legitimate websites do not store information such as login user names or passwords or personal information such as social security numbers or credit card information. Note, however that some websites do use cookies to implement (Keep me logged in or (Remember my password on this computer) features, without actually storing the confidential information within the cookie itself.
Cookies themselves are not harmful; they contain no executable code, cannot become infected, and cookies never run on your computer. They do bring up privacy concerns, however. When you access an Internet site, that website can access ALL of the cookies on your computer, not just the site you're currently visiting. This allows, for example, websites such as Google or Yahoo, to determine which websites you've previously visited in order to customize the display of their own sites. A shopping website may be able to determine recently searched for items from other shopping sites. Websites can also share cookies with each other and read and write each others cookies.
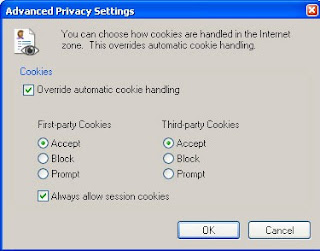
Cookies are easily disabled, but be aware that some Internet pages will not work without them, and some sites will deny you access unless you enable cookies. In Internet Explorer 7 or 8, click on Tools, Internet Options, select the Privacy Tab and then click on the Advanced button. Check the box to override automatic cookie handling, then decide to accept, block, or prompt each time when a website wants to store a cookie on your computer. Note that third-party cookies are created in situations where, for example, you visit msn.com, but the MSN site includes content embedded from another website, and that site (the third-party) stores a cookie on your computer. Session cookies are those that are used while you browse from page to page within a single website - otherwise, you could add items to a store shopping cart (for example) but the items would be gone by the time you¹re ready to go to the checkout page.
You can delete existing cookies by clicking on Tools, Internet Options, and in the Browsing History section of the General tab click on the Delete button. Cookies will be individually recreated the next time you visit the originating websites.


-------------------------------------------------
Friday, October 2, 2009
Looking for a New Phone System?
| Looking for New Phone System? We can help... |
|
|
Monday, September 28, 2009
ABA Online: How a Solo Gained More than 600 Facebook Fans for His Fledgling Firm
The following article was written by Debra Cassens Weiss and posted by ABA Journal Online
A solo practitioner in Massachusetts who struck out on his own about six months ago already has more than 600 Facebook fans for his law firm.
Solo lawyer Richard Vetstein tells the ABA Journal that the accomplishment, touted in a press release, has “absolutely” brought in new business. His goal was to promote his new law firm, the Vetstein Law Group in Framingham, and his blog, the Massachusetts Real Estate Law Blog.
Read the entire article here
-------------------------------------------------
Wednesday, August 5, 2009
"White" Paper Explanations for Legal Technology Questions
http://www.law.com/jsp/legaltechnology/whitepapers.jsp
-----------------------------------------------
Wednesday, June 24, 2009
WBA Tech Tip of the Month: Website Certificates

When you visit what is known as a Secure website, perhaps the only indication you notice is that the web address at the top of your browser has changed from http:// to https://. In the background, however, a series of exchanges take place to ensure that the website is legitimate and the communication between your computer and the Internet is secure.
Prior to the website initially being published, the site owner contacts a third-party Certificate Authority (CA) such as Verisign, Equifax, or one of dozens of other trusted sources, whose job is to ensure that, when your browser points to http://www.microsoft.com/, you really are viewing http://www.microsoft.com/. The website publisher registers with the CA, verifying its identity and the identity of the website. In return the CA issues to the website a unique digital certificate.
When you now visit a secure page on a website, that site sends to your computer its digital certificate. Your browser next contacts the Certificate Authority to verify that the certificate you received is valid for the website you're visiting. This happens automatically, and in most cases your browser simply displays the secure web page. However, if there is a problem with the digital certificate, the browser displays a warning message advising not to proceed to the website.
Certificate errors happen if the information contained within the certificate doesn¹t match the website you¹re visiting: for example, you're visiting http://www.verizon.net/, but the digital certificate was issued to http://www.verizon.com/; or, the certificate has expired (they must be periodically renewed by the website publisher); or, if the certificate has been tampered with. The certificate error displayed by the browser indicates the nature of the problem.
You may also receive a certificate error when visiting your secured internal office website. Typically, this happens because publishers of strictly internal websites don¹t register the site with a Certificate Authority; instead, they create their own digital certificates. When your browser visits this site, it receives a certificate which it is unable to verify via a third party, and you see a warning advising you not to proceed. In this one exception, if you are absolutely certain you are at the correct website, you may click to proceed past the certificate error.
Whenever you visit a website requesting personal information (social security numbers, credit card information, etc.) be absolutely certain the site is legitimate. Only go to sites that you know and trust. Make sure the link at the top of your browser shows https and not http (this indicates that the communication is encrypted). Finally, verify that your site is secure and has a good digital certificate - look for the image of the closed lock (at the top of the window in Internet Explorer 7 and at the bottom in earlier versions; in Internet Explorer 8, click on Safety from the top menu and select Security Report).
Monday, June 8, 2009
WBA Tech Tip of the Month: Clean Up Email Folders to Improve Mail Performance
Empty your email Deleted Items folder frequently (deleted emails do not move to the Windows Recycle Bin). The Deleted Items folder IS NOT a storage location for your saved emails; if you want to hang onto your emails, create additional folders and save your mail there, not in the Deleted Items Folder.
Your Inbox should never have more than your most current emails. Whenever you access this folder, Windows regenerates the Œview¹; the more emails within the folder, the more memory needed to display the information and the longer the processing time required. Once you exceed a few thousand emails, processing time starts counting in minutes rather than seconds. The same is true of the Sent Items folder. Although people don¹t typically view this folder, every sent email gets copied here (assuming this feature is turned on). The greater the number of emails already in that folder, the longer it takes to add another one.
Create subfolders under Inbox and Sent Items and move older emails out of the main mail folders. In Outlook or Outlook Express, simply right-click on Inbox or Sent Items, create a New Folder, give it a name and click OK. Drag email(s) to the new folder. In Outlook, you can also us the email Archive feature, which automatically moves older emails from the Inbox and Sent Items folders to a separate Archive folder structure located below your normal folder list.
-------------------------------------------------
Monday, March 9, 2009
WBA Tech Tip of the Month: Email Spoofing
Spoofing describes fraudulent email activity where the Sender and other information is altered to appear as though the email came from someplace else. It¹s comparable to postal mail examples (and almost as easy to achieve), where someone sends thousands of mass mailings but disguises the return address on the envelope.
The typical reaction from most people is that their computer must be infected with a virus or spyware, causing the computer to send out unsolicited emails. But, in fact, what's taking place has nothing to do with you or your computer.
That also means there isn't much you can do to prevent spoofing. The best you can do is to verify that it really isn't you sending the emails - check your email Sent Items folder, make sure your virus software is working and up to date, and in an office environment ask your network administrator to verify that the emails aren't coming from your workstation.
Otherwise, take a deep breath, knowing that eventually the emails will stop, when the person who is actually generating them finally gets caught by his/her Internet or email Service Provider.
------------------------------------------------
Tuesday, February 24, 2009
WBA Tech Tip of the Week: Accessing Microsoft Office 2007 Documents
Accessing Microsoft Office 2007 Documents
With the release of Office 2007, Microsoft introduced new file formats for
Word (Docx), Excel (Xlsx), PowerPoint (Pptx), and Access (Accdb). Many users
receiving these documents via email or disk can¹t open them because they
have an older version of Microsoft Office or use WordPerfect for their word
processing.
Individuals using Office 2000, Office XP, or Office 2003 can download and install the Office 2007 File Converter software, available free from Microsoft¹s website. Go to www.microsoft.com, access the link for the Microsoft Download Center, and search for the Microsoft Office Compatibility Pack. Or, type Œdownload Microsoft office compatibility pack¹ in a Google search and follow the links. Download and install the software, and from now on you¹ll be able to open Office 2007 documents using your earlier versions normal File, Open dialog box.
WordPerfect¹s latest X4 version can access Office 2007 documents directly.
If you have an older version of WordPerfect, a pre-2000 version of Microsoft
Office, or don¹t have Office at all, you can also download and install
Microsoft¹s Word Viewer 2007 utility (again, either from Microsoft¹s
download site or, in Google, search for ŒWord Viewer 2007 download). You
need both the Word Viewer program and the File Converter software. Once both
are installed, you load Word Viewer, locate and open the 2007 document,
click Edit, Select All and then Edit, Copy.
Then bring up your older version of Office or WordPerfect (or any other Windows based word processor) and click Edit and Paste.
-------------------------------------------------
Monday, February 16, 2009
WBA Tech Tip of the Month: Arrange Your Start Menu Icons Alphabetically
In Windows XP, when you click on Start and then Programs or All Programs, you first see your most recently accessed programs; if you then click on the double-down arrows to see all of your programs, they’ll appear in a haphazard order, typically in the order in which they were installed (Note that in Windows Vista the system automatically displays your program shortcuts in
alphabetical order).
To arrange your Start Menu icons alphabetically, click on Start and then on Programs (for the
Classic XP Interface, or All Programs for the ‘New’ XP Interface). Right-click on any one of the
items listed (it isn’t necessary to click on the double-down arrow here) and select ‘Sort by Name’. The next time you view your programs they’ll be arranged in alphabetical order with folders first (alphabetically), then individual program shortcuts (another difference with Vista, which lists the individual programs first, then the program folders).
Courtesy of Erie County Bar Association and Richard D. Vasil, Vasil Consulting
------------------------------------------------
Wednesday, January 28, 2009
WBA Tech Tip of the Month: Computer Troubleshooting - First Steps
Surveys indicate that 75 percent of all computer problems are resolved by simply restarting the
computer, yet the majority of even veteran users fail to undertake this common-sense first step
prior to contacting IT technical support.
Unlike hard-wired electronic devices, computer software ‘circuits’ are dynamic and selfmodifying, and as programs interact with users and other programs, logic paths are altered and can, under some conditions, degrade or become corrupted. Restarting the computer clears
memory registers and resets the computer logic back to a previous stable condition.
Remember that restarting Windows (also known as rebooting) is not the same as shutting down
and restarting the entire computer, and when the former fails, it is sometimes necessary to attempt the latter. Windows is smart enough to know whether it is restarting from a power-down or power-up condition, and the housekeeping routines it employs are different depending on its previous condition. That’s why a Start, Shutdown, Restart is much faster than a Start, Turn Off, Power On procedure, but not always as effective in correcting certain computer problems.
Also, the newest ‘green’ computers don’t really shutoff when you perform a shutdown or press
the power button - they simply descend into a hibernation state. To completely reset the
computer, it is sometimes necessary to perform a shutdown, then physically disconnect the power cord and wait 10-15 seconds (in order to discharge the capacitors inside). This is similarly true when troubleshooting problems with printers, which in most cases are reset only by removing power to them, not by simply pressing the On/Off button.
Courtesy of Erie County Bar Association and Richard D. Vasil, Vasil Consulting
-------------------------------------------------------------------------------------
